How to Monitor File Transfers: Stopping Data Leaks with MonitUp
Did you know that 88% of data breaches involve human error when transferring sensitive files? Businesses need to monitor file transfers effectively to protect their valuable information. Remote work has expanded the digital perimeter, making it easier for sensitive data to slip through the cracks undetected.
Data leaks often start innocently an employee emails a confidential document to their personal account or uploads sensitive information to an unsecured cloud service. Consequently, these actions can lead to serious security incidents, regulatory fines, and damaged reputations. For small and medium businesses, detecting data leaks early is particularly crucial since they typically have fewer resources to recover from security breaches.
Employee activity monitoring tools like MonitUp offer a solution by tracking file movements across all channels—whether through email, cloud services, or removable devices. Furthermore, these systems help prevent data exfiltration by identifying suspicious patterns and alerting administrators before damage occurs.
This article explores how businesses can strengthen IT security for SMBs through proper file transfer monitoring, identify warning signs of potential data leaks, and implement effective controls using MonitUp's comprehensive tracking capabilities.
Understanding File Transfer Risks in Remote Work Environments
Remote work environments have dramatically expanded the risk surface for data security. File transfers outside traditional office boundaries often lack the robust protection mechanisms found within corporate networks, creating multiple avenues for sensitive information to escape.
Common File Transfer Channels: Email, Cloud, USB
File sharing occurs through various channels, each presenting unique security challenges. Email remains one of the most frequently used methods despite being notably vulnerable to interception. Unencrypted attachments can be easily captured during transmission, especially when sent over public networks.
Cloud-based platforms like Google Drive, Dropbox, and OneDrive offer convenience but introduce "shadow data sprawl" when employees create or share files without proper governance. These files often remain publicly accessible or shared beyond intended audiences indefinitely without detection.
USB devices and external storage media continue to pose significant security threats despite advances in cloud technology. These physical devices enable massive data exfiltration without network detection, making them particularly dangerous. A single flash drive can transfer gigabytes of proprietary information in seconds, completely bypassing network security controls.
How Unmonitored Transfers Lead to Data Leaks
When file transfers go unmonitored, businesses face substantial risks. According to recent data, the average cost of a data breach has risen to $4.88 million, representing a 10% increase from the previous year. This financial impact stems from various consequences:
Inadequate visibility creates dangerous blind spots. Without monitoring file movement across networks, organizations cannot detect unauthorized transfers of sensitive data. Additionally, unmonitored file sharing often results in:
- Compliance violations with regulations like GDPR and HIPAA, resulting in hefty fines
- Unauthorized access through weak passwords and inadequate authentication
- Persistent public links that remain active long after they're needed
Remote workers frequently transfer files without the same level of security found on corporate networks. While files stored internally might be protected through encryption, the same level of security rarely applies when shared remotely. This security gap makes sensitive information vulnerable during transit between locations or devices.
Real-World Examples of Insider Threats via File Sharing
Insider threats manifest in both malicious and accidental forms. In 2017, a Boeing employee emailed a spreadsheet to his wife seeking help with formatting issues. Unknown to him, hidden columns contained personal information of approximately 36,000 colleagues. This accidental breach cost Boeing an estimated $7 million in credit monitoring services for affected employees.
Similarly, Microsoft faced a serious threat when several employees inadvertently exposed login credentials to the company's GitHub infrastructure. This mistake could have given attackers access to Azure servers and internal Microsoft systems, potentially resulting in GDPR fines up to €20 million had European customer data been compromised.
In another case, two General Electric employees downloaded thousands of files containing trade secrets from company servers, then uploaded them to cloud storage or sent them to private email addresses. After FBI investigation, both were convicted and ordered to pay $1.4 million in restitution.
These examples highlight why organizations must monitor file transfers across all channels. Whether malicious or accidental, unmonitored file movement represents one of the most significant security vulnerabilities in today's distributed work environment. Effective file transfer monitoring tools provide the visibility needed to detect suspicious activities before they escalate into costly data breaches.
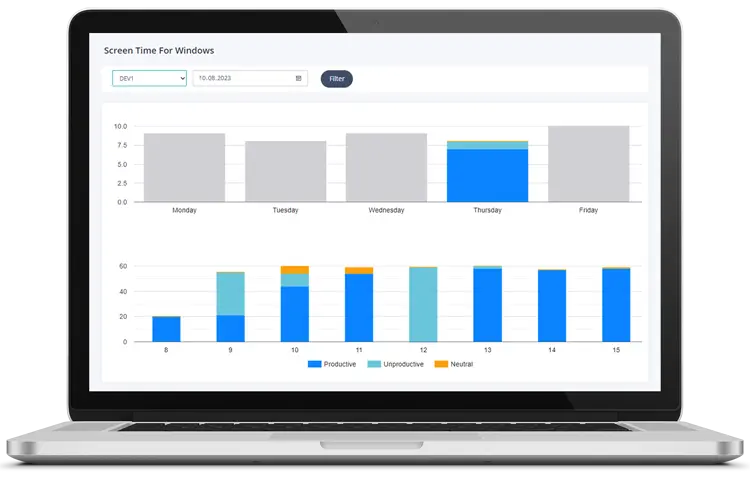 |
|
|
How MonitUp Detects and Logs File Transfers
MonitUp offers robust file transfer monitoring capabilities that act as a first line of defense against data leakage. This software implements multiple layers of tracking technologies to provide visibility into file movements, regardless of where or how they occur.
File Movement Tracking Across Local and Cloud Drives
MonitUp creates a comprehensive monitoring environment by tracking file transfers across multiple storage locations. The system meticulously records all file movements between local drives, network shares, and external storage devices. This multidimensional approach ensures nothing slips through the cracks.
Unlike basic monitoring tools, MonitUp extends its tracking capabilities to cloud environments. The software can scan for files that have been created, modified, deleted, or simply exist within specific folders on the network, SFTP servers, FTP/s servers, Amazon S3 Buckets, and Azure Blob storage. This extensive coverage is essential as organizations increasingly rely on hybrid storage solutions.
For local environments, MonitUp monitors file activities across Windows file servers, failover clusters, and workgroup environments. The software automatically logs every instance when files are copied or moved, creating a detailed record that includes:
- Which file was transferred
- Who initiated the transfer
- When the transfer occurred
- The source and destination locations
Moreover, MonitUp helps detect unusual file renaming or encryption patterns that often precede data exfiltration attempts. By monitoring file transfers comprehensively, administrators gain valuable insights into potential security risks that would otherwise remain hidden.
Real-Time Alerts for Unauthorized File Sharing
Beyond passive monitoring, MonitUp provides active protection through its real-time alerting system. The software can be configured to trigger notifications immediately when suspicious file-sharing activities occur. These alerts enable IT teams to respond quickly to potential threats, effectively stopping data breaches before they escalate.
The notification feature is highly customizable, allowing organizations to set specific parameters for what constitutes suspicious behavior. For instance, MonitUp can flag when unauthorized applications are used or when specific keywords appear in transferred documents. The system can also take automatic screenshots every five minutes for designated employees, providing visual evidence of file-handling activities.
Of particular importance, MonitUp identifies unusual patterns such as file downloads from unfamiliar locations, high-frequency access attempts, or attempts to access sensitive information from untrusted devices or IP addresses. These behaviors often indicate compromised accounts or active data exfiltration efforts.
Audit Trails for File Access and Modifications
Complete accountability requires detailed documentation of all file interactions. MonitUp creates comprehensive audit trails that track every operation performed on monitored files, including viewing, editing, printing, cut/paste actions, and even screen captures.
These audit logs include forensic-level details such as:
- The exact time of each file operation
- IP addresses where files were accessed
- Machine names involved in the transfer
- Complete file paths and locations
- User identities associated with each action
Through these detailed audit trails, MonitUp allows organizations to maintain compliance with regulatory frameworks such as GDPR, PCI, and other regional data privacy legislation. Additionally, these logs prove invaluable during security investigations, enabling administrators to trace the exact sequence of events surrounding any suspicious file transfer.
For even greater security oversight, MonitUp allows integration with Security Information and Event Management (SIEM) tools, enabling consolidated audit reporting and mapping of file-level protection policies to business workflows. This integration creates a unified security monitoring environment that significantly improves threat detection capabilities.
Technical Indicators of Suspicious File Activity
Effective data leak prevention hinges on recognizing key technical signals that precede exfiltration attempts. MonitUp monitors file transfers by tracking several suspicious activity patterns that frequently indicate potential security incidents.
Unusual File Renaming or Encryption Patterns
Attackers often rename or encrypt files as part of data exfiltration or ransomware attacks. MonitUp identifies these suspicious patterns by analyzing file properties and behaviors. Files suddenly renamed with high-entropy extensions (random-appearing characters) typically signal ransomware activity. The system automatically compares file extensions against known malicious patterns and generates alerts when matching suspicious extensions.
Sudden changes to multiple files simultaneously warrant immediate investigation. Indeed, MonitUp can detect when legitimate files with standard extensions (.jpg, .pdf, .docx) are converted to unusual formats. This pattern recognition is critical as attackers increasingly use file transformation techniques to conceal data before extraction.
Security incidents like the ".devil" ransomware illustrate why monitoring file extension changes is vital - in that case, attackers modified extensions across multiple servers, simultaneously disabling antivirus protection.
Off-Hours File Transfers and Remote Access
File transfers occurring outside normal business hours represent a critical indicator of potential data theft. Naturally, MonitUp flags activities like large data transfers during nights, weekends, or holidays when normal operations are minimal.
The MISL data breach provides a clear example of why timing matters - the perpetrator accessed large quantities of sensitive data primarily during off-hours, a pattern that should have triggered immediate alerts. Subsequently, this behavioral anomaly became a recognizable indicator of malicious intent.
MonitUp establishes baseline patterns for each user and department, enabling the system to detect when file access deviates from established norms. Unusual login times combined with excessive file access attempts create a high-confidence indicator of compromise.
Use of Unauthorized File-Sharing Tools
Organizations often face threats from employees using unapproved file-sharing applications. These unauthorized tools create security blind spots that bypass corporate data protection mechanisms.
MonitUp identifies when employees utilize:
- Personal cloud storage accounts (Dropbox, Google Drive, OneDrive) outside IT-approved instances
- File transfer services like Transfer.sh that evade corporate monitoring
- Removable media connections attempting to extract large data volumes
- File enumeration tools that scan multiple network shares
Critically, MonitUp detects attempts to discover shared folders and files across networked systems - a reconnaissance technique often preceding data theft. This "File Share Enumeration" activity represents a classic first step before malicious actors attempt to extract valuable information.
By monitoring these technical indicators, organizations can identify potential data exfiltration attempts before sensitive information leaves their network, thus maintaining both security posture and regulatory compliance.
Using MonitUp to Prevent Data Exfiltration
Beyond detecting suspicious activity, MonitUp offers powerful preventive tools that actively block data exfiltration attempts. These features work together to create multiple layers of protection for sensitive information.
Blocking Unapproved File Transfer Applications
MonitUp effectively controls which applications can access and transfer company data. This capability targets shadow IT—unauthorized software that employees might use to circumvent security protocols. The system identifies and blocks unapproved applications attempting to move files outside the network.
Specifically, MonitUp can:
- Block personal cloud storage services like unauthorized Dropbox or Google Drive instances
- Prevent usage of unsanctioned file transfer tools
- Restrict file uploads to unapproved cloud services
For browser-based transfers, MonitUp supports configuration that redirects users to approved browsers when accessing sensitive content. This restriction ensures files are only uploaded through channels where proper monitoring and protection mechanisms exist.
Setting File Access Permissions by Role
Role-based access control (RBAC) forms the cornerstone of MonitUp's preventive strategy. This approach aligns with the principle of least privilege, granting employees access only to the data necessary for their specific job functions.
Through MonitUp's permission management interface, administrators can:
- Create granular access controls at directory and file levels
- Establish role hierarchies that reflect organizational structure
- Apply Windows access control lists (ACLs) for fine-grained permissions
RBAC implementation through MonitUp drastically reduces the risk surface, as employees cannot transfer files they cannot access in the first place. Moreover, this structured approach simplifies onboarding and offboarding processes by making it easier to update access rights when job functions change.
Automated Alerts for Large File Transfers
Unusual file transfer volumes often signal potential data exfiltration. Hence, MonitUp allows configuration of automated alerts based on various thresholds, including file size and transfer frequency.
Administrators can customize alert parameters based on:
- Maximum allowable file sizes for transfer
- Number of transfers within a specified timeframe
- Specific file types or extensions being moved
Once triggered, these alerts enable rapid response to potential exfiltration attempts. The system can be configured to take immediate action, from blocking the transfer outright to notifying security personnel for further investigation.
Furthermore, MonitUp integrates with existing security infrastructure, feeding alert data into Security Information and Event Management (SIEM) systems for comprehensive threat response coordination. This holistic approach ensures that suspicious file transfer activities are promptly addressed before sensitive data leaves the organization.
Benefits of File Transfer Monitoring for Compliance and Security
Implementing robust file transfer monitoring delivers substantial regulatory and security benefits beyond basic threat detection. Organizations face increasing scrutiny regarding how they handle sensitive information, making compliance a business-critical function rather than just a checkbox exercise.
Meeting GDPR and HIPAA Data Handling Requirements
Regulatory frameworks impose strict requirements on data handling processes. GDPR mandates breach reporting within 72 hours of discovery, while HIPAA allows up to 60 days. This significant difference highlights why organizations handling data across jurisdictions must implement comprehensive monitoring systems.
File monitoring tools provide essential capabilities to satisfy these regulations:
- Detailed logging of who accessed files, when modifications occurred, and why changes were made
- Documentation of processing activities that can be presented to supervisory authorities when needed
- Enforcement of compliance with data privacy laws through technical safeguards
Organizations operating in regulated industries must demonstrate proper controls over sensitive information. Accordingly, file monitoring systems generate evidence that security measures are actively enforced, satisfying auditor requirements for both GDPR and HIPAA compliance.
Reducing Insider Threat Risk with Visibility
Insider threats represent a costly security challenge, with annual losses reaching USD 15.40 million per incident. Comprehensive file monitoring reduces this risk through increased visibility into user behavior.
Throughout the organization, monitoring systems detect potential warning signs:
- Unauthorized access attempts to sensitive documents
- Unusual file renaming or encryption patterns
- Attempts to use personal cloud storage for corporate data
This visibility enables organizations to identify malicious or negligent behavior early. Undeniably, early detection minimizes financial consequences and brand damage, allowing security teams to intervene before data leaves organizational boundaries.
Improving Employee Accountability and Audit Readiness
File transfer monitoring establishes clear accountability chains. Whenever security incidents occur, detailed audit logs allow precise tracking of who accessed what information and when.
Audit readiness requires maintaining extensive records of file-related activities. These logs prove invaluable during:
- External compliance audits
- Internal security investigations
- Forensic analysis after security incidents
Beyond regulatory requirements, these audit trails help identify process weaknesses and training opportunities. Organizations can use this data to strengthen security practices and demonstrate due diligence to stakeholders.
Primarily, monitoring systems provide definitive proof of compliance efforts, helping organizations avoid penalties that can reach €20 million or 4% of annual turnover under GDPR.
Conclusion
File transfer monitoring stands as a critical defense mechanism against data leaks. Throughout this article, we've examined how unmonitored file sharing creates substantial security vulnerabilities, especially in remote work environments. Consequently, businesses face increasing risks of sensitive information escaping through email attachments, cloud services, and removable media.
MonitUp addresses these challenges head-on with comprehensive tracking capabilities. The system monitors file movements across local and cloud drives, generates real-time alerts for unauthorized sharing, and maintains detailed audit trails for all file activities. Additionally, it identifies technical warning signs such as unusual encryption patterns, off-hours transfers, and usage of unapproved applications.
Most importantly, MonitUp shifts organizations from reactive to proactive security postures. Rather than merely detecting breaches after they occur, the platform actively prevents data exfiltration through application blocking, role-based access controls, and automated alerts for suspicious transfers.
The benefits extend beyond basic security. Businesses using file transfer monitoring meet strict regulatory requirements under frameworks like GDPR and HIPAA. This compliance readiness reduces potential fines while strengthening overall security governance. Visibility into file movements likewise minimizes insider threat risks and establishes clear accountability chains.
Data security demands vigilance across all transfer channels. Though cybersecurity threats continue evolving, tools like MonitUp provide the essential visibility needed to protect sensitive information. File transfer monitoring thus becomes not merely a technical solution but a fundamental business necessity for organizations committed to protecting their most valuable digital assets.